You probably just got an error like this:
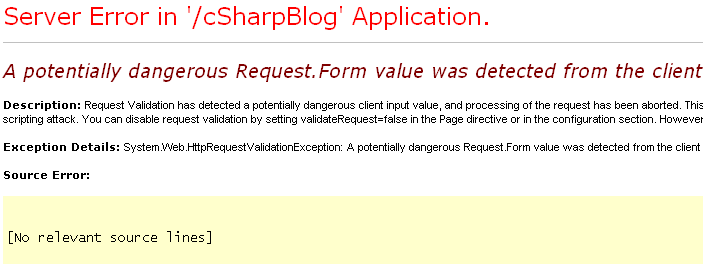
A potentially dangerous request? Oh noes!
This may confuse you at first, but it's actually pretty simple. C# detected that a variable we were populating from a POST request was being fed with markup. In this case it was html, but it could've been javascript or even embedding objects like Flash, Java or Silverlight. Any of these things can be really, really bad. So C# tries to protect you by throwing this error and stopping web page execution. So how do you fix it? The answer is actually in the error description. We have to edit the .aspx page and add validateRequest=false into the page directive.
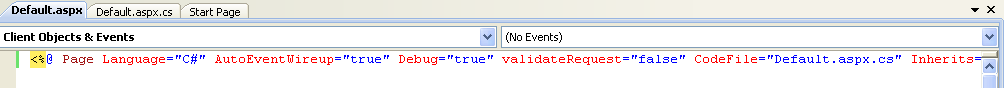
No more error
There we go, now it works. So wait...what about comments? Do we really want random internet people to be able to post javascript and html into comments? Oh no, definitely not. However, with the validateRequest=false we just added, they can do just that. What we need to do is filter their inputs and strip out any illegal content like html and javascript. So how do we do that? Actually, we already have a sanitize() method just for that. So let's make some changes to it.
public enum clean{
DB, TAGS
}
private string sanitize(string value, clean type)
{
switch (type)
{
case clean.DB:
value = value.Replace("'", "''");
break;
case clean.TAGS:
value = Regex.Replace(value, @"<(.|n)*?>", string.Empty);
break;
}
return value;
}
DB, TAGS
}
private string sanitize(string value, clean type)
{
switch (type)
{
case clean.DB:
value = value.Replace("'", "''");
break;
case clean.TAGS:
value = Regex.Replace(value, @"<(.|n)*?>", string.Empty);
break;
}
return value;
}
We start by altering our clean enum to have another option called TAGS. I could've called that anything, but TAGS works for me. We then add a new case into the switch statement and do a Regex against the value that should strip our tags out for us. In order to add Regex I had to add a new namespace... just type Regex, then wait for Visual Studio to have a little red underline under the bottom of the Regex word. Hover over it and you should get the option to add the namespace automatically. Alternately you can just manually add the System.Text.RegularExpressions namespace.
Regex is an extremely complicated subject, one I'm not versed well enough in to write a tutorial on at this time. However, there are plenty of options out there for a decent tutorial. Check out this page for some great information.